Your Cryptocurrency Portfolio Can Vanish Overnight If You Are Not Aware About This
When bitcoin, the first cryptocurrency, was launched, its developers and earliest adopters were filled with optimism about blockchain technology as a way to counter the powerful distrust that they held for banks and middlemen. Designed with sophisticated encryption, irreversible transactions and a decentralized structure, cryptocurrency technology was supposed to be unhackable.
Unfortunately, the system upon which it is built has proven to be vulnerable to resourceful criminals and human error.
The security gaps that have become apparent over time have made cryptocurrency owners ask:
- How many types of crypto-related security vulnerabilities are there?
- Do I need to become a technical wizard to keep my coins safe?
- What is the most common type of security problem?
- How can I reduce the risk to my cryptocurrency holdings?
- What resources do I need to reduce crypto-related security risks?
This guide is designed to provide current and prospective cryptocurrency owners with answers to these questions and other information that reduces security risk. (The guide is contributed by BitIRA Team)
Keeping Your Cryptocurrency Safe
From the beginning, when the software underlying the Bitcoin protocol was launched in 2009, cryptocurrency ownership has provided investors with an exciting experience. Much of that excitement came from factors such as an extreme potential for gain (or loss) in coin value or the possibility of government regulation. These factors were and are beyond investor control.
The risk of security breaches is another matter. Investors have significant control over the risk of losing their coins in a security breach. There are no guarantees, of course. But every cryptocurrency investor can dramatically reduce the risk of security-related losses by using a combination of vigilance, knowledge, and discipline.
As Cryptocurrency Values Rise, So Does the Need for Security
Someone once asked Willie Sutton, a famous American bank robber, why he robbed banks. He supposedly replied, “That’s where the money is!”
In much the same spirit, the frequency and value of security breaches against cryptocurrency owners and service providers are going up. Why? Because the number of users and the value of digital coin are increasing, too.
Consider these 2017 cryptocurrency statistics gathered by The Telegraph newspaper in the UK:
- As the price of bitcoin rose from less than $1,000 to nearly $20,000 during 2017, crimes linked to it more than tripled from 320 to 999 in one year.
- 1 in 10: That’s the chance that an owner of the cryptocurrency would be affected by a scam.
- $225 million, the total investor losses to phishing scams.
- 30,000 owners scammed by Ethereum-related cybercrime alone. Losses averaged $7,500 per owner.
- $390 million of wealth lost to cybercriminals.
Keeping coins safe is an essential part of investment success. This guide is designed to help current or prospective cryptocurrency investors detect, avoid and (sometimes) recover from security vulnerabilities.
How Cryptocurrency Holders Lose Their Investment
While cryptocurrency promoters accentuate only the positive aspects of owning coin, this guide has a different purpose. We’ve assembled a comprehensive list of security problems, which could occur when you invest in cryptocurrencies. No, we’re not being cruel. In future sections, we’ll also mention how you can detect or avoid cryptocurrency-related loss and crime.
Here are the scenarios of the dark side of cryptocurrency investing—the different ways that individuals and service providers fall victim to security vulnerabilities:
Investors can lose their coin by:
- Forgetting or losing coded access information.
- Lacking the security awareness or resources that help keep their investment safe.
Criminals, increasingly specialized and sophisticated ones, are the more likely culprits. They:
- Get access to cryptocoin validation codes and don’t give them back until the coin owner pays a fee.
- Divert computer resources of cryptocurrency owners (often without their knowledge) and use them in money-making schemes.
- Trick owners into thinking that criminals are legitimate service providers, cryptocurrency startups or other owners of the coin.
- Break into digital storage spaces and divert cryptocurrency to their own storage accounts.
- Fool cryptocurrency owners into behavior that helps the crooks get information about coin accounts, access to it or coin itself.
- Engage investors of cryptocurrency startups in Ponzi schemes.
- Infect otherwise benign websites or ads with malware, which gets access to cryptocurrency keys.
These scams and misfortunes are variations on the themes of theft, deception and malicious software. You’ll find descriptions of each problem and ways to detect or prevent it in Section 3, “Facing the Challenges of Cryptocurrency Security.”
Cryptocurrency Concepts You Should Know
Before diving into the how-to details of Section 3, “Facing the Challenges of Cryptocurrency Security,” you might want to review some basic ideas that cryptocurrency security is based on. In each case, we’ll provide the basic idea, how it relates to security methods and refer you to other sources if you want more details.
“Sources and Resources,” Section 4 of this guide, will point you to this additional information.
Cryptocurrencies and the Blockchain
We’re assuming that you are familiar with these essential concepts. But, if you need to refresh your memory, you can find excellent materials here.
Cryptocurrency Encryption and Storage
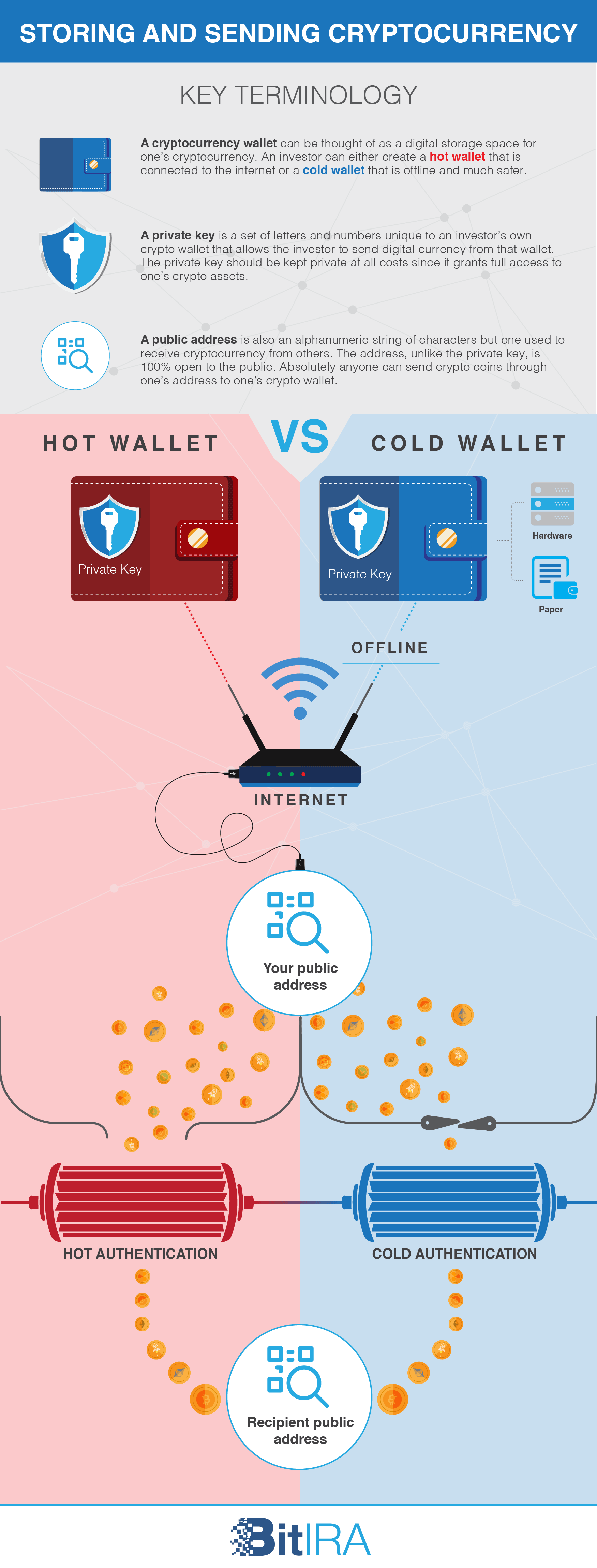
In cryptocurrency markets, protecting and storing coins are vital elements of the currencies’ success. Complex codes provide the protection, and digital exchanges and wallets provide storage between currency transactions.
Encryption
Encryption “hides” data by converting data only a computer can read to encrypted data that humans can read. The coded version can be used only if users have another code, which transforms the data back into a format that humans can read. These codes are called keys.
Asymmetric cryptography
In two-key encryption (also known as public key encryption), security is based on two pieces of information, a public-private key pair.
The first or public key provides the location of cryptocurrency stored on the internet. The second or private key decrypts the content of stored cryptocurrency. This data, which is stored on the blockchain, validates the location, ownership and amount of currency at that location.
Private key data is the object of cybercriminals’ desire. Many of the tactics we describe in Section 3 involve breaking through security measures to possess private keys. That’s because cryptocurrency has no physical form, such as dollars or euros do.
The key to understanding cryptocurrency security is this: Whoever has this private key validation information owns the currency.
Wallets
No matter which type of cryptocurrency you invest in, you’ll need to store the all-important private key information somewhere.
The “something” you store it in is a digital wallet, a must-have part of cryptocurrency investment. That “somewhere” can be online storage in a wallet or with a third-party storage service, called an exchange. Offline storage on paper or a hardware device is other (many say more prudent) alternatives.
Level of security risk. The longer that the device that stores your private key is connected to the internet, the higher the risk of losing your cryptocurrency investment.
- Hot wallets are stored at online exchanges and accessed with apps or a Web browser. They are “hot” because they are connected to the internet, which makes them more vulnerable to security breaches and malware attacks.
- Cold wallet is a method of storing coins offline (not connected to the internet). This approach eliminates the opportunity for hackers to use an internet connection to break into a digital wallet and steal private key information.
- Hardware wallets are small cold wallet devices that often look like USB drives. They are physical storage devices you can use for cryptocurrency transactions. Each hardware wallet comes paired with a private key, which gives you access to the transaction validation data. Without access to the blockchain and its information, your coins are inaccessible.
- Paper wallets. This term describes the practice of writing private key information onto paper and storing it in a safe place offline.
Ideally, you would use two digital wallets, each for a different purpose. Use a hot wallet briefly to perform coin trades and transactions. Use the cold wallet (also known as cold storage) approach when you want to store your savings long-term.
Also, it’s a security best practice to back up both wallets’ private keys and store them offline in a safe place.
Cryptomining
When the first cryptocurrency system was set up and launched in 2009, it included a potential for up to 21 million bitcoins. Since then, only 17 million BTC are in use.
Cryptomining is the way that new cryptocurrency coins (also known as tokens) are released into circulation. The cryptomining process includes gathering and verifying recent transactions of bitcoin or other forms of cryptocurrency into blocks and adding them to the blockchain digital ledger.
The process requires miners to solve an extremely complex puzzle—whoever solves the puzzle first gets the coin. Staying competitive with other crypto miners, however, requires a computer with specialized hardware, lots of computer processing power and energy resources.
The opportunity for cryptomining fraud lies in:
- Hackers stealing coin directly from legitimate cryptomining companies.
- Tricking current or potential cryptominers to buying nonexistent computer hardware (phishing attacks).
- Cloud mining companies renting their equipment to cryptocurrency miners at prices higher than what they will actually earn. They provide “profits” by taking the coin’s value from new investors (equipment renters). This is a classic Ponzi scheme.
Cryptocrime Tactics
If you keep track of cryptocurrency technology and business news, you know there’s a long list of crimes, spoofs and shady dealings that relate to cryptocurrency. Here’s a list of terms to help you stay informed. How many do you recognize?
-
- Social engineering. This is a general term that describes a criminal entity fooling a target into doing something to the criminal’s advantage. Because social engineering is a means to an end, it is the prelude to other tactics such as ransomware or cryptojacking.
- Phishing. This tactic occurs when a criminal presents a target with a false pretext that can be a person, company, government agency or organization. In cryptocurrency investments, phishing attacks can progress to ransomware or various types of digital wallet break-ins that involve stealing credentials or private keys.
- Cryptojacking. This tactic involves diverting a target’s resources, without their permission. In cryptocurrency environments, cryptojacking usually involves diverting the computer CPU resources of coin holders to mine cryptocurrencies.
- Breaking into online wallets and exchanges. This tactic involves using different means (false identities in phishing attacks for example), to get private key information.
- Malvertising. The name tells the story. In this tactic, malicious ads are used to spread malware through criminally controlled online advertisements. The goal: to compromise web browsers and their plug-in.
- ICO exit scams. Establish a new cryptocurrency. Publicize it and persuade investors to buy some. Reward folks who refer new investors with cash and tokens. Then, disappear. That’s the recipe of a standard initial coin offering (ICO) scam. If it sounds like a Ponzi scheme, you’re right.
- Poisoned website. This term describes a website that delivers malware as an ad on a website.
- Phone porting. This tactic is a wild mix of phishing, hacking and outright breaking and entering into wallets. Hackers snoop around social media, looking for cryptocurrency-related conversations, in which investors lost their phone and email information. Then, posing as the victim, scammers call up the target’s phone provider. The goal: to fool the customer service representative into transferring the phone number to a device that the hacker controls.
- When the hackers take over the phone number, they can go into the victim’s cryptocurrency exchange account. They compromise the password and use the phone number for second-factor authentication. After that, it’s a matter of diverting investor funds to their wallets.
- Spear phishing. This is a focused phishing scam targeted at a specific person or organization. The phishing attack can precede data theft, or cybercriminals might use it to install malware on a target’s computer.
Securing Your Coin at Home and When You Trade
Some analysts consider offline (cold storage) wallets the only safe way to invest in cryptocurrency. If you’re talking about holding coin for the long term, offline storage is the safe way to go. But sooner or later, your coin must emerge from hibernation and be transferred to another wallet or an exchange.
Here are general tips that will help you keep your coin safe, wherever it might be.
Isolate Your Investment
There are ways to keep your coins safe when you store them at home or transfer them during a transaction.
When security measures refer to using a dedicated computer—one that only transfers cryptocurrency into and out of a digital wallet—the computer is protected by an air gap. This security measure refers to computers or networks that are not connected directly to the internet or to any other computers that are connected to the internet.
Securing your coin this way is a simple process. You connect the (ideally new and unused) computer to the internet, complete the cryptocurrency transaction, disconnect the computer from the web immediately and use it for nothing else—ever.
Protect Yourself When You Trade Cryptocurrency
In addition to the isolation methods described above, use these tactics when you move coin into or out of your digital wallet:
- Secure your operating system. Install it on a new computer or scrub your hard drive and reinstall your OS on a machine you already own.
- Find and use a good password manager. It’s easy to mistype private keys, which can be more than 50 characters long. No one is perfect. Buy a memory aid and sleep soundly. See here.
- Use two-factor authentication on every device that transfers or accepts cryptocurrency. See here.
- Get an offline (hardware) wallet. It’s the safest way to hold your investment between transactions. See here.
- Use a virtual private network (VPN) whenever you authorize the transfer of cryptocurrency-related information. VPNs encrypt the network path between your coin and its destination.
It’s always a good idea to use a VPN whenever you’re on a coffee shop or other network that you don’t control.
Facing the Challenge of Cryptocurrency Security
Bitcoin stands out as the oldest and the most successful cryptocurrency. But, a wide range of security concerns about BTC is emerging, because it’s vulnerable to illegal transactions or attacks within online storage pools and exchanges.
The Bitcoin protocol we know today was built on the proof-of-work principle, in which transactions can be processed securely on a decentralized, peer-to-peer network. But, without a central collection institution such as a bank, cryptocurrency mining and transaction processes are not entirely secure.
Stay Alert, Get Educated
As you read through the how-to descriptions below, stay alert to methods that require technical knowledge or abilities. Then get educated (or engage an experienced security specialist). You don’t have to be a tech wizard to protect your cryptocurrency. There are no guarantees, but the more security awareness you develop, the lower your risk of something going wrong.
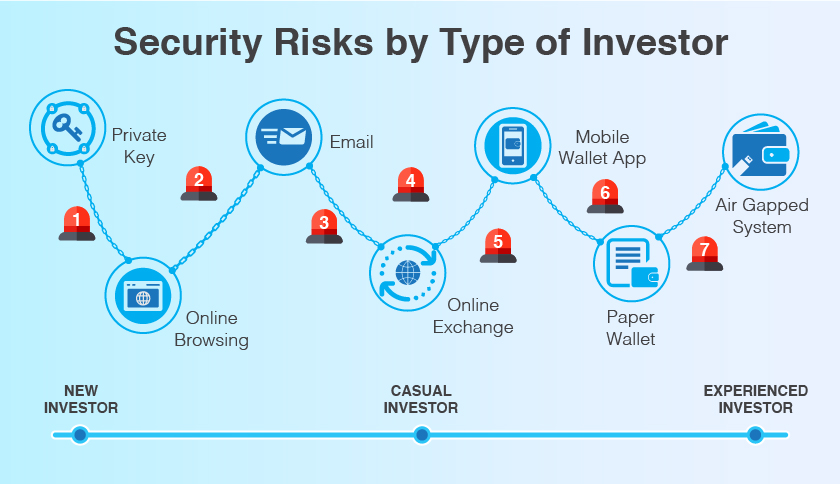
7 ways that accidents or weak security can put your cryptocurrency investment at risk.
1: Forgetting or Losing Cryptocurrency Keys
Cryptocurrency ledgers do not have a central documentation method. If you lose access to your digital wallet or its digital keys, there is no way to recover lost cryptocurrency.
Lose Your Keys, Lose Your Investment
Yikes, you’ve lost or forgotten your all-important private key to your cryptocurrency investment! How did that happen? It’s surprisingly easy. All it takes is:
- Locking yourself out of your online wallet and losing access to your password reset email address that gets you back into your wallet.
- Damaging or losing a paper copy of your private keys.
- Forgetting your password or losing your multi-factor authentication data when you set up a new hosted wallet on an exchange.
- Storing the backup copy of keys in the same location as your daily-use keys and then losing, damaging or destroying both copies by accident.
Prevent loss of your keys by…
Being what some folks might call a bit paranoid. That means:
- Storing the backup and daily-use copies of your wallet keys in different locations. Extremely cautious cryptocurrency investors back up their backup copies.
- Not printing out your keys. Instead, rely on handwritten “paper wallet” backups. Printers can store print jobs, which could then be hacked. If you control your own private keys, make a paper backup and store it in a personal safe or a bank safe deposit box.
- Use true air-gapped cold storage. Never connect your computer to the internet but do generate private key information offline. You don’t have to be online to generate a valid address. Use a program on the air-gapped system. Then, copy the public key information and signed transactions by using a USB.
Prevention is the only cure. There is no recovery.
2: Theft by Ransomware
NiceHash said it lost about $64 million worth of bitcoin during an attack on its systems in December 2017. The Slovenian bitcoin trading marketplace enables customers to mine for cryptocurrencies by leveraging unused CPU cycles of their computer equipment.
Theft via ransomware is the reason why many businesses are putting ransomware defense high on their security priority list. Now, cryptocurrency investors should be aware of ransomware, too. While ransomware isn’t as popular as it was–some attackers, like those behind XiaoBa have abandoned it–cryptocurrency ransomware remains a threat to individual investors and small businesses.
What is a ransomware attack?
Ransomware occurs when the malicious software enters your computer and holds your data or access to it, hostage until you pay. Because cryptocurrencies are unregulated, hackers can remain anonymous. To make them even more anonymous, crooks often demand payment in other digital currencies such as Monero.
How often do ransomware attacks occur? Often. And, as cryptocurrency values increase and ransomware-as-a-service resources become more common, it occurs more often than ever.
Non-technical hackers often engage ransomware developers, paying them a portion of the proceeds. That way, the crooks make money without skills or investing money to launch a malicious attack.
Reducing the Risk of Ransomware Attacks
Usually, attackers notify you—when it’s too late—with a message that no one wants to receive.
But you can learn to recognize exploits that enable ransomware attacks. Take screenshots of your digital exchange accounts and offline digital wallet files. Learn to spot differences between these images and emails you receive from phishing artists. And never follow links from emails unless you are expecting the message. Go to the site directly on your own.
Change the Odds of Ransomware in Your Favor
There are many ways you can patch and protect your IT infrastructure to avoid ransomware attacks. These measures will help keep you out of trouble:
- Set up your operating system for automatic updates. The first step to avoiding ransomware is to update your operating system, which often includes new security capabilities. Automating this task eliminates a task on your to-do list.
- Install an anti-malware solution. A no-brainer? Yes. But, many ransomware strains still leave a digital signature. Anti-malware solutions can use these signatures to discover and block threats before you are locked out of your wallet.
- Update anti-malware software regularly. By using software patches to keep your anti-malware software current, you can block exploit kits from finding weaknesses and running ransomware attacks on your computers. Make sure to run security solutions that detect known and unknown threats.
- Avoid suspicious links and email attachments. Ransomware attacks often begin with phishing. You click a malicious email link and get redirected to a compromised website. Best practice: don’t click suspicious links and email attachments, especially from senders you don’t know.
- Disable macros used by Microsoft Office documents. Digital attackers often hide ransomware executables in Office macros. Protect your coins by disabling Office macros and steering clear of unsolicited attachments and macros generally.
- Install a pop-up blocker. Bad actors rely on email and malvertising for delivery. Install an ad blocker onto your devices and use it to prevent the automatic opening of ads on all sites that you visit.
- Back up your data to both a cloud service and a hard drive. That way, you have a copy that’s available anywhere there’s internet access and a copy that’s physically accessible all the time. Both types of storage are relatively inexpensive and will certainly prove their value if you ever become a ransomware target.
- Establish and use air gaps. Consider a different approach to cryptocurrency security by adding air gaps to your system.
Recover from Ransomware Attacks
If you are a victim of ransomware, you can also use anti-malware tools to clean your computers of ransomware before you restore your data. Ransomware recovery tools are easily available online, some at no cost. However, this strategy works only if you have backed up your data before disaster strikes.
3: Theft of Resources via Cryptojacking
In January 2018, researchers discovered the Smominru cryptomining botnet, which infected more than a half-million machines, mostly in Russia, India, and Taiwan. The botnet targeted Windows servers to mine the Monero cryptocurrency. Cybersecurity firm Proofpoint estimated that by the end of January, the botnet had generated coin worth about $3.6 million in value.
Criminals are also using ransomware-like tactics and poisoned websites to get your computer to mine cryptocurrencies for them.
Cryptojacking, the Vampire Cybercrime
If there’s an aspect of cryptocurrency security that has a sci-fi flavor, it has to be cryptojacking, the unauthorized use of your computer resources.
Cryptojacking takes the form of a malicious infection, which steals your CPU resources to perform cryptomining on behalf of criminals—without your permission
Criminals use phishing-like tactics to trick targets into loading cryptomining code onto their computers. Or, they inject a malicious script into a website or an ad that’s delivered to many websites. Sometimes, hackers use both methods to maximize their return.
NOTE: Some analysts include ransomware and outright theft of cryptocurrency in the cryptojacking category. But, we use the narrower definition of cryptojacking, which involves the only cryptomining.
Detecting Cryptojacking
Unlike the ransomware attacks, which provide notices from hackers, the signs of cryptojacking can be subtle. That’s why you should:
- Train yourself in cryptojacking threat awareness. But don’t count on your existing endpoint protection tools. Desktop antivirus tools won’t detect these threats.
- Watch for overheating in your devices (including thin mobile ones, like tablets and smartphones). Heat from excessive CPU use might cause the processor or cooling fan failures.
- Monitor your IT infrastructure for unexplained CPU activity levels. Watch for a big spike in CPU usage when you get onto and off your network.
- Consider deploying a network monitoring solution. Cryptojacking is easy to detect with a network perimeter monitoring solution that reviews all web traffic. Think of monitoring software as another cost of cryptocurrency investment.
How to Avoid Cryptojacking
Unlike other security-related problems in this guide, cryptojacking has no direct effect on your cryptocurrency investment. Instead, it drains your CPU, which can cause system crashes, lag time and poor network performance.
However, you need your IT infrastructure to make and manage your digital currency That why sub-par performance due to cryptojacking becomes a cost of your cryptocurrency investment.
But there is good news. You can take active measures to avoid cryptojacking or at least detect it quickly:
- Install an ad-blocking or anti-cryptomining extension on web browsers. Cryptojacking scripts are often delivered through web ads. Consider extensions designed to detect and block them.
- Keep your web filtering tools up to date. If you identify a web page that is delivering cryptojacking scripts, make sure that users are blocked from accessing it again.
- Maintain browser extensions. Some attackers use malicious browser extensions or poison legitimate extensions to execute cryptomining scripts.
Stop the Flow of Resources
In the case of cryptojacking, you stop the undercover theft of resources rather than recover your investment. Take these steps as soon as you confirm cryptojacking in your computer:
- Kill and block website-delivered scripts. If you are hit by an in-browser JavaScript attack, kill the browser tab that runs the script. First, notice the website URL that’s the source of the script and update your web filters to block it. Then, consider deploying anti-cryptomining tools to prevent future attacks.
- Update and purge browser extensions. If an extension infected your browser, update all the extensions and remove those that are infected or not needed.
If you need help to implement these tips, consider engaging an experienced IT specialist.
4: Phishing for Cryptocurrency
Phishing is a popular blockchain exploit that infects mobile wallet apps and online exchanges, where cryptocurrency is stored. Phishing is a means to an end—getting you to expose keys or other sensitive information without your knowing it.
Worms and trojan malware are often spread through phishing email scams. These are designed to trick you into opening email attachments containing viruses or clicking links to fake websites posing as legitimate ones.
From there, hackers steal your sign-in credentials or infect your computer with malware. In recent months, fraudsters have written specialized phishing lures to penetrate these systems.
What Phishers Are Looking For
Phishers are looking for administrative passwords or private keys, either of which would give them access to investors’ wallets. Cryptocurrency-related phishing occurs often, especially with increasing bitcoin prices.
- Overall, around 9 percent of Kaspersky Lab users worldwide were attacked by phishing.
- In 2017, the Kaspersky Lab Anti-Phishing system was triggered 59,569,508 times on the computers of Kaspersky Lab users.
- Kaspersky Lab researchers detected 13 million more phishing attacks on customers’ computers during Q32017 than the previous three months.
The attacks occurred mainly in the financial sector. Targets included banks, payment services, and online stores.
Watching for Phishing Attacks
A watchful eye and common sense are the two best tools for detecting a phishing attack. Before you click that email link:
- Learn to identify phishing emails. Take screenshots of emails from cryptocurrency exchanges and other businesses that handle cryptocurrency-related information. Use them to spot differences between legitimate sites and emails you might receive from phishing artists.
- Check the source of information of the incoming email message. What information does the sender want? For example, would a legitimate bank ask for it?
- Make sure the sender is who they say they are. Contact the sender on a separate email thread.
- Make sure you’re the only recipient. In phishing messages, the name in the TO field is often blank or filled with someone else’s name.
- Watch out for emotional content. Phishing messages often contain threatening language or an urgent request for an immediate response or personal information.
- The message has an attachment.
5: Breaking and Entering Into Your Digital Wallet
At 2:57 a.m. on January 28, 2018, in Tokyo, someone hacked into the digital wallet of Japanese cryptocurrency exchange Coincheck Inc. and pulled off one of the biggest heists in history. After the theft of nearly $524 million in digital tokens, authorities started talking about more regulation. And, they started recognizing the advantages of decentralized ways of trading.
This break-in highlights two problems of the global cryptocurrency market. Cryptocurrency exchanges around the world vary wildly in terms of their level of information security expertise. And, some digital wallets are not adequately secure.
How Criminals Break Into Digital Wallets
Cryptocurrency investors usually store their coins in an encrypted storage space called a digital wallet. There are several forms of digital wallets in use today. They include:
- Hot wallets, which are stored at cryptocurrency exchanges and accessed via apps or a Web browser.
- Cold wallets (also known as cold storage).
Cybercriminals can deceive cryptocurrency owners into downloading malware disguised as a digital wallet. When the target opens the malware file, its code uses a fake registration process to request personal account information.
While the currency owner thinks that the wallet session is normal, the malware moves the coin from the investor’s wallet to the crook’s, before the investor notices that anything is wrong.
Here are the ways that cybercriminals break into digital wallets:
- Cryptocurrency-stealing malware. This new malware category specializes in one activity, stealing cryptocurrency. The malware code can steal login credentials or the wallet itself or divert coins in the middle of a legitimate transaction.
- Initial coin offering (ICO) fraud. Given the hundreds of cryptocurrencies in circulation, it’s easy for criminals to create a fake ICO and arrange for investors to “buy into” their new venture.
This is what happened in December 2017, when the SEC shut down the PlexCoin ICO, which the agency claims were a $15 million fraud.
Hackers can also impersonate (spoof) a legitimate ICO and trick investors into paying them instead of the real company.
- Phone-porting. This exploit occurs when criminals engage in cell phone identity theft. They take control of a person’s phone number by tricking a telecom provider into giving them control of the user account. When the crooks have control of the phone number, they reset the password and route the coins to their own digital wallet.
- Fake digital wallets. Digital wallets are an absolute must-have in cryptocurrency investment. Problem is, fake wallets occasionally appear online or in mobile app stores. When targets download their coins to these fakes, criminals can steal their investment.
Avoid Digital Wallet Breaking and Entering
Preventing digital wallet break-ins requires doing your homework and getting a bit obsessive about digital security. That means:
- Performing due diligence. Before investing in an ICO, do your homework. Check the track record of a claimed ICO. Avoid too-good-to-be-true offers, especially if you received them via email or the social media grapevine.
- Improving your digital wallet security. Add a unique PIN and verification question to your account. Even better, switch your two-factor authentication from SMS to a third-party service such as Google Authenticator. But, the best solution is to store your coins offline and use a hardware wallet.
- Hardening your computer security. Use a robust antivirus program and an inbound/outbound firewall to protect your computer. Include two-factor authentication and a password manager to protect the login process. Finally, take additional measures, such as a virtual private network (VPN), which encrypts your internet connection.
- Considering a dedicated computer. By limiting a device to just one function—moving your cryptocurrency—you’ll keep transfers simple and possibly avoid a lot of grief.
6: Theft by Social Engineering
In June 2017, the most popular Ethereum Classic exchange started stealing money from users’ wallets. Hackers used social engineering methods to convince the exchange managers that they were the real owners. After breaking into the exchange, the hackers started intercepting cash flows.
Luckily for the wallet owners, the crooks diverted those flows immediately—which alerted exchange managers that something might be wrong. The exploit was discovered and stopped, and wallet holders got their coins back.
Many Paths, One Goal: Digital Deception
Unfortunately, happy endings like this are rare. Like phishing, social engineering methods are means to an end—separating cryptocurrency owners and their coins. And like phishing, there are many ways to accomplish this goal.
The key to social engineering lies in scammers convincing digital wallet owners or service providers that the scammers are the legitimate wallet owners. After establishing their “identity,” the scammers then use different strategies to divert cryptocurrencies to their own wallets.
Trust is Worth Its Weight in Cryptocoins
Social engineering-based exploits are based on scammers presenting cryptocurrency investors with false identities. That makes it essential that you know who you are dealing with—at every stage of buying, storage and selling cryptocurrency.
To detect social engineering scams, look for the tried-and-true recipe of:
- The promise of easy money.
- A sense of urgency—the “act now or lose the opportunity!” gambit.
- Asking you to become a partner in shady dealings.
To avoid social engineering scams, know who and what to trust. That means:
- Always confirm identities, companies, and resources. If you want to purchase a cryptocurrency mining rig, be sure to buy it from a trusted source with a known transaction history and reputation.
- If you want to invest In someone else’s cryptomining operations (a highly risky venture), be sure you can see and verify their public mining address. Have them send proof they possess the proper equipment. Then, do research to confirm that this equipment will do the job.
- Stay on the right path. Navigate to known, good links, and avoid clicking on links that are sent to you.
- Use your common sense. Question any offer that sounds too good to be true.
But what about securing your computer system? You can do a lot to reduce the risk of false identities. In general, learn how to secure your social media accounts and look for the source of cryptocurrency-related social media content.
7: Sending Funds to the Wrong Address
After losing their cryptocurrencies, some investors say they’ve sent their cryptocurrencies to the wrong address. After all, they claim, their private and public keys are a long string of numbers and letters. They typed in at least one wrong character. As a result, their currency was routed to an unknown address, and they’re out of luck.
Is this what happened? Maybe, but probably not.
Avoiding Typos
Given a built-in checking process in the coin transfer software, mistyped characters would prevent the app from sending coins off into cyberspace in the first place. You can prevent this misfortune, but you must be prepared before anything goes wrong.
To avoid typos, get and use password management software and use the copy and paste functions carefully. Check your destination twice before you hit Send.
More likely, a user would lose their coin by sending it to a wallet that holds a related cryptocurrency (bitcoin to a bitcoin cash wallet for example). Theoretically, this problem can be solved. In the real world, you’re probably out of luck.
Avoiding Fraud or Theft
Unfortunately, you are more likely to lose track of your coin by sharing your private key with a criminal–without your realizing it. Misplaced trust, not bad typing, sends coins into an unchangeable, one-way trip to someone else’s wallet. People claim loss by typo because it’s much easier to explain the loss with a typing error than an error in judgment.
Stay informed with daily updates from Blockchain Magazine on Google News. Click here to follow us and mark as favorite: [Blockchain Magazine on Google News].
Get Blockchain Insights In Inbox
Stay ahead of the curve with expert analysis and market updates.
latest from tech
Disclaimer: Any post shared by a third-party agency are sponsored and Blockchain Magazine has no views on any such posts. The views and opinions expressed in this post are those of the clients and do not necessarily reflect the official policy or position of Blockchain Magazine. The information provided in this post is for informational purposes only and should not be considered as financial, investment, or professional advice. Blockchain Magazine does not endorse or promote any specific products, services, or companies mentioned in this posts. Readers are encouraged to conduct their own research and consult with a qualified professional before making any financial decisions. The featured image used is just a creative depiction of the title and it does not intend to hurt sentiments of any person or institution. If it hurts anyone sentiments, please do not hesitate to reach out to Blockchain Magazine.

 Bitcoin
Bitcoin  Ethereum
Ethereum  XRP
XRP  Tether
Tether  Solana
Solana  USDC
USDC  Dogecoin
Dogecoin  Cardano
Cardano  Lido Staked Ether
Lido Staked Ether  TRON
TRON  Chainlink
Chainlink  Wrapped Bitcoin
Wrapped Bitcoin  Sui
Sui  Wrapped stETH
Wrapped stETH  Avalanche
Avalanche  Stellar
Stellar  Hedera
Hedera  Toncoin
Toncoin  Shiba Inu
Shiba Inu  LEO Token
LEO Token  Hyperliquid
Hyperliquid  Bitget Token
Bitget Token  Litecoin
Litecoin  WETH
WETH  USDS
USDS  Polkadot
Polkadot  Bitcoin Cash
Bitcoin Cash  Ethena USDe
Ethena USDe  MANTRA
MANTRA  Wrapped eETH
Wrapped eETH  Uniswap
Uniswap  Ondo
Ondo  Pepe
Pepe  Monero
Monero  Aave
Aave  NEAR Protocol
NEAR Protocol  WhiteBIT Coin
WhiteBIT Coin  Mantle
Mantle  Official Trump
Official Trump  Aptos
Aptos  Dai
Dai  Internet Computer
Internet Computer  Ethereum Classic
Ethereum Classic  Bittensor
Bittensor  Cronos
Cronos  OKB
OKB  POL (ex-MATIC)
POL (ex-MATIC)  Gate
Gate