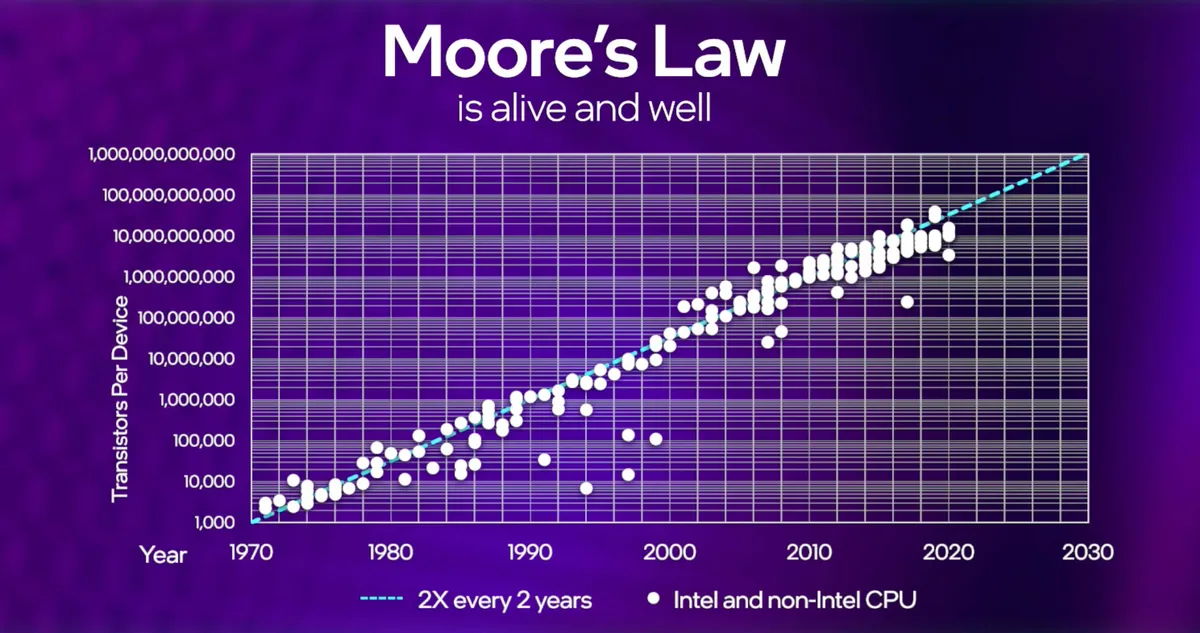
What Is Moore’s Law, And How Does It Impact Cryptography?
Moore’s Law, coined by Gordon Moore in 1965, is an empirical observation that has become a guiding principle in the world of computing. It states that the number of transistors on a microchip doubles approximately every two years, leading to a continuous and exponential increase in computing power. While Moore’s Law has fueled the rapid advancement of technology, its implications extend beyond hardware performance to the field of cryptography. In this comprehensive article, we explore Moore’s Law, its historical context, and the profound influence it exerts on cryptographic methods and security paradigms.
Understanding Moore’s Law:

Gordon Moore, co-founder of Intel Corporation, first articulated his observations about the growth of transistor count in a 1965 paper. He noted that the number of transistors on a microchip had been doubling approximately every two years, leading to a corresponding increase in computing power. This trend, later dubbed Moore’s Law, has held remarkably true over several decades, driving the exponential growth of computational capabilities.
The Impact on Hardware and Computing Power:

Moore’s Law has been a driving force behind the relentless progress in computer hardware. The continual increase in transistor density has enabled the development of faster, smaller, and more powerful microprocessors. This, in turn, has fueled advancements in areas such as artificial intelligence, data processing, and, significantly, cryptography.
1. Processing Speed and Cryptographic Algorithms:
The exponential growth in processing speed facilitated by Moore’s Law has directly impacted cryptographic algorithms. Cryptographic methods that were considered secure a decade ago may face vulnerabilities when exposed to the computational power available today. As processors become faster and more efficient, cryptographic algorithms need to evolve to withstand the increasing threat of brute-force attacks.
2. Encryption Standards and Key Length:
One of the notable impacts of Moore’s Law on cryptography is the need for longer key lengths to maintain the same level of security. As computational power increases, the time required to break encryption using traditional methods decreases. Consequently, encryption standards have had to adapt by recommending longer key lengths to resist attacks and ensure the confidentiality of sensitive information.
3. Evolution of Cryptanalysis Techniques:
The rapid progression of Moore’s Law has not only affected the development of cryptographic algorithms but has also influenced cryptanalysis techniques. Adversaries with access to formidable computational resources can employ more sophisticated and powerful attacks, necessitating a continuous arms race between cryptographic defenders and potential attackers.
4. Quantum Computing and Shor’s Algorithm:
While not a direct consequence of Moore’s Law, the principles of exponential growth in computational power have heightened concerns about the potential impact of quantum computing on cryptography. Shor’s algorithm, a quantum algorithm developed by Peter Shor, threatens the security of widely used cryptographic schemes, such as RSA and ECC, by efficiently factoring large numbers. The advent of quantum computers, when they arrive, could render existing cryptographic methods obsolete.
5. Post-Quantum Cryptography:
The prospect of quantum computing has spurred research into post-quantum cryptography, which focuses on developing cryptographic algorithms that can resist quantum attacks. The field aims to establish new standards that will secure communication and data in a quantum computing era. The influence of Moore’s Law on the development of quantum-resistant algorithms underscores the interconnected nature of hardware capabilities and cryptographic methodologies.
Also, read – Your Ultimate Guide To Becoming A Crypto Lawyer
Challenges and Considerations in the Face of Moore’s Law:

While Moore’s Law has been a catalyst for unprecedented technological progress, particularly in the realm of computational power, it has presented a set of challenges and considerations, especially within the domain of cryptography. As the exponential growth in computing capabilities continues, organizations and researchers must navigate these challenges to ensure that cryptographic methods remain resilient and effective in the face of evolving threats.
1. Rapid Advancements Outpacing Standards:
One of the significant challenges posed by Moore’s Law is the rapid pace at which computational power advances, often outpacing the development and standardization of cryptographic algorithms. As hardware becomes more powerful, cryptographic methods that were once considered secure may become vulnerable to attacks. This necessitates a constant reassessment of encryption standards and the development of new, more robust algorithms to stay ahead of potential threats.
2. Key Lengths and Brute-Force Attacks:
The increase in computing power afforded by Moore’s Law has a direct impact on the effectiveness of brute-force attacks. As processors become faster, the time required to exhaustively search through possible keys in cryptographic algorithms decreases. This prompts the need for longer key lengths to maintain the same level of security. However, longer key lengths come with their own set of challenges, such as increased computational overhead and potential compatibility issues.
3. Quantum Computing Threats:
While not an immediate consequence of Moore’s Law, the overarching principles of exponential growth in computational power heighten concerns about the potential impact of quantum computing on cryptography. Quantum computers, when realized, could leverage algorithms like Shor’s algorithm to efficiently break widely used cryptographic schemes, rendering them obsolete. Preparing for the advent of quantum computing requires the development and adoption of quantum-resistant cryptographic methods.
4. Implementation Challenges and Side-Channel Attacks:
The practical implementation of cryptographic algorithms is susceptible to various challenges, including side-channel attacks. These attacks exploit information leaked during the execution of cryptographic operations, such as power consumption or electromagnetic radiation. As computational power increases, the sophistication of side-channel attacks also rises, necessitating meticulous attention to the secure implementation of cryptographic algorithms.
5. Balancing Security and Performance:
Organizations face the ongoing challenge of striking the right balance between security and performance. While robust cryptographic algorithms enhance security, they can introduce computational overhead. This trade-off becomes more pronounced as computational power increases. Achieving optimal performance without compromising security requires careful consideration of the specific requirements and constraints of the application or system.
6. Standardization and Global Collaboration:
The global nature of the digital landscape underscores the importance of international standardization and collaboration in addressing cryptographic challenges. Achieving consensus on standardized cryptographic algorithms ensures interoperability and a unified approach to security. However, achieving such standardization can be challenging, given diverse geopolitical considerations, varying threat landscapes, and differing perspectives on privacy and security.
7. Continuous Research and Development:
Moore’s Law necessitates continuous research and development in the field of cryptography. The landscape is dynamic, with new vulnerabilities emerging alongside technological advancements. Staying ahead of potential threats requires a commitment to ongoing research, collaboration, and innovation to develop cryptographic methods that can withstand evolving attack vectors.
8. Privacy Concerns and Ethical Considerations:
As cryptographic methods evolve, so do concerns about privacy and ethical considerations. Striking a balance between providing robust security measures and respecting user privacy is an ongoing challenge. Encryption protocols must be designed with privacy in mind, addressing potential vulnerabilities that could compromise user data while upholding ethical standards in the use of cryptographic technologies.
While Moore’s Law has undeniably propelled technological progress, it brings forth a set of challenges and considerations for the field of cryptography. The need for constant vigilance, adaptation, and innovation is evident as organizations and researchers grapple with the delicate balance between leveraging the benefits of computational progress and maintaining the security and privacy of digital systems. Successfully navigating these challenges requires a collaborative and interdisciplinary approach, bringing together experts from fields ranging from computer science and mathematics to ethics and international relations. As we forge ahead into an era of ever-increasing computational capabilities, the challenges presented by Moore’s Law underscore the imperative for a resilient and adaptive approach to securing the digital landscape.
Most powerful exponential force? 😳
In hardware, the most powerful exponential force is Moore’s Law. In finance, it’s compounding interest. In software, it’s composability. @a16z @coinchangeio #crypto #defi
— Maxim Galash 🛡️| Coinchange.io (@maxgalash) April 16, 2023
Is Moore’s Law Still Relevant in 2023?

As we step into 2023, the relevance of Moore’s Law, the foundational principle of exponential growth in computing power, continues to echo through the corridors of technological innovation. Gordon Moore’s observation in 1965 about the doubling of transistors on a microchip every two years has been a driving force in shaping the trajectory of computing capabilities. However, its relevance in 2023 is not without nuanced considerations, particularly given the evolving landscape of the semiconductor industry and its far-reaching impact on sectors like cybersecurity, cryptocurrency, and blockchain networks.
1. Evolution of Moore’s Law:
Moore’s Law has historically been a reliable predictor of the growth in computing power, but in recent years, its traditional formulation has faced challenges. The miniaturization of transistors has approached physical limits, leading to modifications of the law. Some experts propose a “More than Moore” approach, emphasizing innovations beyond traditional transistor scaling, such as 3D stacking, specialized accelerators, and novel materials.
2. Semiconductor Industry Challenges:
The semiconductor industry, a linchpin of Moore’s Law, has encountered challenges in maintaining the pace of transistor density growth. Issues like manufacturing costs, heat dissipation, and quantum effects at smaller scales have prompted a reevaluation of traditional semiconductor scaling. Despite these challenges, advancements in semiconductor technologies persist, driven by innovative solutions that extend the applicability of Moore’s Law.
3. Cryptocurrencies and Blockchain Networks:
Moore’s Law influences the security and scalability of cryptocurrencies and blockchain networks, playing a pivotal role in their development. The computational power required for consensus mechanisms, such as proof-of-work (PoW), is influenced by the availability of powerful hardware. The doubling of computational capabilities has direct implications for the efficiency of mining operations and the overall security of blockchain networks.
4. Cryptographic Implications:
In the realm of cryptography, Moore’s Law has both positive and challenging implications. On one hand, the increased computational power strengthens the security of certain cryptographic algorithms, enabling more complex encryption methods. On the other hand, it necessitates continuous adaptation, as faster processing capabilities render certain encryption standards vulnerable to brute-force attacks. This dynamic interplay between computational progress and cryptographic methods shapes the security landscape.
5. Quantum Computing’s Influence:
While not directly tied to Moore’s Law, the emergence of quantum computing poses a paradigm shift in computational capabilities. Quantum computers, when realized, could solve certain problems exponentially faster than classical computers, challenging the security of existing cryptographic methods. Preparing for this quantum era requires a reevaluation of cryptographic standards, emphasizing post-quantum cryptography.
6. Artificial Intelligence and Data Processing:
In the realm of artificial intelligence (AI) and data processing, Moore’s Law has been a catalyst for the training and execution of complex machine learning models. The exponential growth in computational power enables the handling of massive datasets and the development of sophisticated AI algorithms. This convergence of Moore’s Law with AI has profound implications for various industries, including healthcare, finance, and autonomous systems.
7. Cybersecurity Challenges:
Moore’s Law’s ongoing relevance introduces cybersecurity challenges. The exponential growth in computational power benefits both defenders and adversaries. While it enables the development of more robust security measures, it also empowers malicious actors with the means to execute more sophisticated attacks. This dynamic landscape requires a continuous cycle of innovation and adaptation in cybersecurity strategies.
In 2023, Moore’s Law stands as a testament to the enduring drive for technological progress. While its traditional formulation may see modifications, the core concept of exponential growth in computing power continues to shape the technological landscape. The semiconductor industry’s responses to challenges, coupled with the interplay between Moore’s Law and emerging technologies like quantum computing and AI, underscore the ongoing relevance and impact of this foundational principle. As we navigate the complexities of an ever-evolving digital era, the legacy of Moore’s Law persists, guiding us through new frontiers of innovation and transformation.
Conclusion:
In conclusion, Moore’s Law has been a driving force behind the transformative growth of computational power, shaping the landscape of technology and, consequently, the field of cryptography. The continuous doubling of transistor counts on microchips has influenced the development of cryptographic algorithms, encryption standards, and the ongoing effort to address emerging threats. As we navigate the ever-evolving intersection of Moore’s Law and cryptography, the imperative remains clear: to adapt, innovate, and stay ahead of the security challenges presented by the relentless march of computational progress. The symbiotic relationship between Moore’s Law and cryptography underscores the dynamic nature of the cybersecurity landscape, where staying secure requires a blend of resilience, foresight, and continuous adaptation.
Stay informed with daily updates from Blockchain Magazine on Google News. Click here to follow us and mark as favorite: [Blockchain Magazine on Google News].
Get Blockchain Insights In Inbox
Stay ahead of the curve with expert analysis and market updates.
latest from tech
Disclaimer: Any post shared by a third-party agency are sponsored and Blockchain Magazine has no views on any such posts. The views and opinions expressed in this post are those of the clients and do not necessarily reflect the official policy or position of Blockchain Magazine. The information provided in this post is for informational purposes only and should not be considered as financial, investment, or professional advice. Blockchain Magazine does not endorse or promote any specific products, services, or companies mentioned in this posts. Readers are encouraged to conduct their own research and consult with a qualified professional before making any financial decisions.

 Bitcoin
Bitcoin  Ethereum
Ethereum  Tether
Tether  XRP
XRP  Solana
Solana  Dogecoin
Dogecoin  USDC
USDC  Lido Staked Ether
Lido Staked Ether  Cardano
Cardano  TRON
TRON  Avalanche
Avalanche  Chainlink
Chainlink  Wrapped stETH
Wrapped stETH  Toncoin
Toncoin  Sui
Sui  Shiba Inu
Shiba Inu  Wrapped Bitcoin
Wrapped Bitcoin  Hyperliquid
Hyperliquid  Stellar
Stellar  Polkadot
Polkadot  Hedera
Hedera  WETH
WETH  Bitcoin Cash
Bitcoin Cash  LEO Token
LEO Token  Uniswap
Uniswap  Litecoin
Litecoin  Pepe
Pepe  Wrapped eETH
Wrapped eETH  NEAR Protocol
NEAR Protocol  Ethena USDe
Ethena USDe  Aptos
Aptos  USDS
USDS  Internet Computer
Internet Computer  Aave
Aave  Cronos
Cronos  POL (ex-MATIC)
POL (ex-MATIC)  Ethereum Classic
Ethereum Classic  Mantle
Mantle  Render
Render  MANTRA
MANTRA  WhiteBIT Coin
WhiteBIT Coin  Monero
Monero  Bittensor
Bittensor  Dai
Dai  Artificial Superintelligence Alliance
Artificial Superintelligence Alliance  Arbitrum
Arbitrum  Ethena
Ethena