Unraveling The Top10 Blockchain Attacks And DLT Vulnerabilities
Blockchain technology, known for its robust security features, has earned a reputation for being highly resilient to attacks. However, it’s essential to understand that the security of blockchain is intrinsically linked to the vulnerabilities of the underlying Distributed Ledger Technology (DLT). In this article, we’ll explore the intricate connection between blockchain attacks and DLT vulnerabilities, shedding light on why these two concepts are inextricably related.
The Foundation: Distributed Ledger Technology (DLT)
DLT serves as the foundational technology for blockchain systems. It’s a decentralized database that records transactions across multiple nodes in a network. Key features of DLT include:
- Decentralization: DLT operates without a central authority, relying on a network of nodes for transaction validation and consensus. This feature enhances security and trust.
- Immutable Record: Data once added to the ledger cannot be altered or deleted. This immutability ensures data integrity.
- Consensus Mechanisms: DLT employs various consensus mechanisms like Proof of Work (PoW) and Proof of Stake (PoS) to validate and add transactions to the ledger.
Blockchain Attacks: A Challenge to DLT
Blockchain attacks encompass a spectrum of malicious activities aimed at compromising the security, integrity, or functionality of a blockchain network. These attacks exploit vulnerabilities within the blockchain infrastructure and can have significant consequences. Some of the most notable blockchain attacks include:
1. 51% Attack: In a Proof of Work (PoW) blockchain, a 51% attack occurs when an attacker gains control of over 50% of the network’s computational power. This allows the attacker to manipulate transactions and potentially lead to double-spending, eroding trust in the system.
2. Sybil Attack: A Sybil attack involves creating multiple fake identities or nodes on a network to gain control or disrupt the network’s consensus. By pretending to be multiple independent participants, an attacker can influence network decisions in their favor.
3. Smart Contract Vulnerabilities: Smart contracts are self-executing pieces of code on blockchains. Vulnerabilities in smart contracts can be exploited to drain funds, disrupt applications, or execute unintended actions, posing a threat to decentralized applications (DApps).
4. Distributed Denial of Service (DDoS) Attacks: DDoS attacks aim to overwhelm a blockchain network by flooding it with traffic. This can render the network temporarily unusable, impacting user experience and causing financial losses.
Also, read – Becoming a Blockchain Specialist: Navigating the Path to Expertise
The Link Between Blockchain Attacks and DLT Vulnerabilities
Blockchain attacks often target vulnerabilities in the underlying DLT. Here’s why they are closely connected:
- Consensus Mechanism Exploitation: Many blockchain attacks manipulate the consensus mechanisms of DLT to compromise the network. For instance, a 51% attack leverages a vulnerability in PoW-based DLT to exert control.
- Smart Contract Weaknesses: Exploiting vulnerabilities in smart contracts, which run on the DLT, is a common attack vector. These weaknesses are rooted in the DLT’s programming, making them a potential entry point for attacks.
- Node Vulnerabilities: The security of individual nodes in a DLT network is critical. Attacks that compromise nodes can affect the entire network’s security.
- Sybil Attacks and Decentralization: DLT’s decentralization, a strength in terms of trust and security, can be exploited through Sybil attacks. A weak DLT structure might not detect fake nodes, compromising the entire network.
The Importance of Robust DLT Design
To enhance the security of blockchain networks, it’s crucial to address vulnerabilities in the underlying DLT. This can be achieved through:
- Consensus Mechanism Choice: Careful selection of consensus mechanisms based on the network’s requirements can mitigate the risk of 51% attacks and ensure the DLT’s security.
- Code Audits: Regular audits of the smart contracts and code running on DLT can identify and fix vulnerabilities, reducing the risk of successful exploits.
- Node Security: Ensuring the security of individual nodes is paramount to protect the network. Employing robust security measures and regular updates is essential.
- Network Vigilance: Staying vigilant against Sybil attacks and monitoring network activity helps maintain DLT’s decentralization and security.
The top 10 blockchain attacks and Distributed Ledger Technology (DLT) vulnerabilities:
1. Smart Contract Vulnerabilities
Overview: Smart contracts are self-executing contracts with code governing the terms of the agreement. They offer efficiency and automation but are complex, making them susceptible to vulnerabilities. High-profile smart contract hacks have resulted in significant financial losses.
Types of Vulnerabilities:
- Reentrancy Attacks: Attackers can repeatedly call a contract before previous calls finish, leading to unauthorized fund transfers.
- Overflow and Underflow: Incorrect arithmetic calculations can occur due to insufficient precision.
- Unchecked Low-Level Calls: External contracts can be manipulated to perform harmful actions.
2. 51% Attacks
Overview: A 51% attack happens when a malicious entity controls over 50% of a blockchain’s computing power. This allows them to manipulate the network, reverse transactions, and undermine the security and trustworthiness of the blockchain.
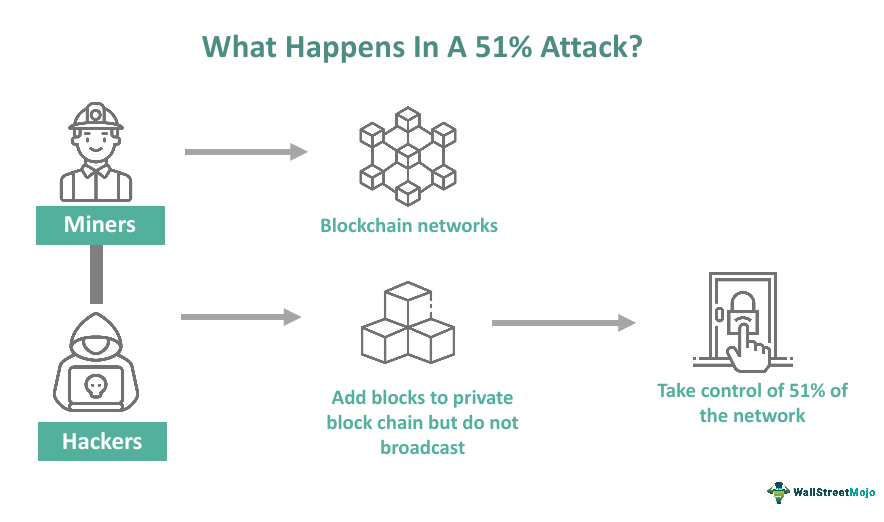
Impact:
- Double Spending: Attackers can spend the same cryptocurrency more than once by reversing transactions.
- Network Manipulation: Transaction history can be rewritten, leading to chaos and distrust in the network.
3. DeFi Exploits
Overview: Decentralized Finance (DeFi) is a booming sector offering innovative financial services. However, its rapid growth has attracted attackers. Recent exploits have led to substantial financial losses and raised concerns about DeFi protocol security.

Common DeFi Vulnerabilities:
- Flash Loan Attacks: Attackers exploit flash loans to manipulate DeFi protocols.
- Reentrancy Exploits: Smart contract vulnerabilities are leveraged to steal assets.
- Oracle Manipulation: Attackers manipulate oracles to distort price data.
4. Cross-Chain Attacks
Overview: Cross-chain bridges enable the transfer of assets between different blockchains, but their complexity can make them susceptible to attacks. Recent hacks on cross-chain bridges have resulted in substantial financial losses.

Common Attack Vectors:
- Exploiting Bridge Vulnerabilities: Attackers exploit weaknesses in the bridge’s code or design to steal assets.
- Misconfigured Cross-Chain Transactions: Errors in the execution of cross-chain transactions can lead to asset loss.
5. Quantum Computing Threat
Overview: Quantum computers, though in early development, pose a significant threat to blockchain security. Their potential lies in their ability to break cryptographic algorithms used in blockchains, potentially allowing attackers to steal funds and manipulate networks.

Impact:
- Breaking Cryptographic Foundations: Quantum computers can potentially break widely-used cryptographic algorithms like SHA-256 and ECDSA.
- Loss of Trust: The emergence of quantum computing could erode trust in existing blockchain networks unless post-quantum cryptographic solutions are implemented.
6. Phishing Attacks
Overview: Phishing attacks are a common method for attackers to gain access to blockchain accounts. Attackers send fraudulent emails or messages that appear to be from legitimate sources, often containing links to malicious websites or attachments that install malware.
Common Targets:
- Exchange Accounts: Phishers target users to steal login credentials.
- Wallet Access: Phishing messages may attempt to compromise wallet security.
7. Rug Pulls
Overview: A rug pull is a scam where developers abandon a cryptocurrency project after raising money from investors. These scams are often difficult to detect, as scammers create elaborate websites and social media accounts to make their projects seem legitimate.
Characteristics:
- False Promises: Rug pull projects promise high returns and gain investor trust.
- Swift Exit: After raising funds, developers disappear, causing financial losses to investors.
8. Supply Chain Attacks
Overview: Supply chain attacks involve targeting the software development process of a blockchain project. Attackers exploit vulnerabilities in the development process, insert malicious code into the project’s software, and compromise the network’s security.
Attack Scenarios:
- Malware Insertion: Attackers insert malware into development tools, infecting the project’s code.
- Trojanized Libraries: Compromised libraries can introduce vulnerabilities into the codebase.
9. Physical Attacks
Overview: Physical attacks on blockchain infrastructure, such as mining farms and exchanges, can disrupt operations and result in the theft of hardware and assets. These attacks have real-world consequences for blockchain networks.
Physical Attack Types:
- Theft: Criminals steal mining equipment or hardware from facilities.
- Sabotage: Physical attacks can disrupt operations, affecting network security.
10. Social Engineering Attacks
Overview: Social engineering attacks manipulate individuals into revealing confidential information or performing actions that compromise their security. These attacks can be used to gain access to blockchain accounts, steal funds, or disrupt operations.
Common Social Engineering Tactics:
- Impersonation: Attackers may impersonate trusted entities to deceive victims.
- Pretexting: Attackers create fabricated scenarios to manipulate individuals into revealing information.
Conclusion
Blockchain attacks are closely related to the vulnerabilities within Distributed Ledger Technology. Understanding this connection is crucial for safeguarding the integrity and security of blockchain networks. As blockchain technology continues to evolve, addressing DLT vulnerabilities and fortifying the underlying technology will remain pivotal in the ongoing battle to protect against malicious attacks. By strengthening DLT foundations, we can enhance the resilience of blockchain systems and ensure they continue to serve as secure and trustworthy platforms for the future.
Stay informed with daily updates from Blockchain Magazine on Google News. Click here to follow us and mark as favorite: [Blockchain Magazine on Google News].
Get Blockchain Insights In Inbox
Stay ahead of the curve with expert analysis and market updates.
latest from tech
Disclaimer: Any post shared by a third-party agency are sponsored and Blockchain Magazine has no views on any such posts. The views and opinions expressed in this post are those of the clients and do not necessarily reflect the official policy or position of Blockchain Magazine. The information provided in this post is for informational purposes only and should not be considered as financial, investment, or professional advice. Blockchain Magazine does not endorse or promote any specific products, services, or companies mentioned in this posts. Readers are encouraged to conduct their own research and consult with a qualified professional before making any financial decisions. The featured image used is just a creative depiction of the title and it does not intend to hurt sentiments of any person or institution. If it hurts anyone sentiments, please do not hesitate to reach out to Blockchain Magazine.

 Bitcoin
Bitcoin  Ethereum
Ethereum  XRP
XRP  Tether
Tether  Solana
Solana  Dogecoin
Dogecoin  USDC
USDC  Cardano
Cardano  Lido Staked Ether
Lido Staked Ether  TRON
TRON  Chainlink
Chainlink  Avalanche
Avalanche  Wrapped stETH
Wrapped stETH  Wrapped Bitcoin
Wrapped Bitcoin  Stellar
Stellar  Sui
Sui  Toncoin
Toncoin  Hedera
Hedera  Shiba Inu
Shiba Inu  WETH
WETH  Polkadot
Polkadot  LEO Token
LEO Token  Litecoin
Litecoin  Bitcoin Cash
Bitcoin Cash  Bitget Token
Bitget Token  Uniswap
Uniswap  Hyperliquid
Hyperliquid  Official Trump
Official Trump  USDS
USDS  Wrapped eETH
Wrapped eETH  Pepe
Pepe  NEAR Protocol
NEAR Protocol  Ethena USDe
Ethena USDe  Aave
Aave  Aptos
Aptos  Internet Computer
Internet Computer  Ondo
Ondo  Ethereum Classic
Ethereum Classic  Mantle
Mantle  WhiteBIT Coin
WhiteBIT Coin  Monero
Monero  Cronos
Cronos  Jupiter
Jupiter  POL (ex-MATIC)
POL (ex-MATIC)  Render
Render  Dai
Dai  MANTRA
MANTRA  Layer One X
Layer One X 




